Tuesday, August 30, 2005
World becoming smaller for Cyber criminals...
 The world is becoming a much smaller place for malicious hackers, virus code writers and "cyber-criminals".
The world is becoming a much smaller place for malicious hackers, virus code writers and "cyber-criminals".Brazilian federal police last week cuffed 85 people across seven states suspected of hacking online bank accounts and netting $33m.
The work which leads to this fast results requires cross border, inter-country cooperation. As the laws for internet security mature around the world this response will become even more effective.
The "Trust" of the internet as a viable platform for conducting business requires these types of actions to take place, quickly, effectively and visibly.
The internet today contains special listening outposts which record all activity at major nodes. These effective packet recorders and archives provide vital information for tracking down the cyber criminals in their activities. One of the names for Earlier project on this activities was: code name carnivore. This project as been since renamed DCS1000 Carnivore spy system.
Full details on carnivore can be found here: Canivore.
There is even a small impersonation of the original covert project nickname carnivore personal edition.
As fast and effective incidence response is one of the key elements of modern internet security, it requires:
- Good customer logging
- Internet Service Provider logging and cooperation
- Cooperation with vendors
- Cooperation Authorities
- Good auditing
- Forensic Analysis
FBI announcement and previous FBI quote"Electronic surveillance has been extremely effective in securing the conviction of more than 25,600 dangerous felons over the past 13 years" .
Saturday, August 27, 2005
Which Anti-virus software should I choose?
 First, is this the right question? Yes, but only partially. Having a good anti-virus solution is not good enough if:
First, is this the right question? Yes, but only partially. Having a good anti-virus solution is not good enough if:- disabled by the end-user
- not configured properly
- if signatures not up to date
- if not monitored properly
- if not integrated into the right process
It is useful to be able to know if your anti-virus software (hardware) is up to the mark.
There are several site which can provide useful information and insight into some of the best antivirus solutions available today:
- Virus Bulletin
- AV-Test Org
- ICSA Labs
- National Institute of Standards and Technology (NIST)
- Anti-virus Information Exchange Network (AVIEN)
Once and Anti-virus is installed it is good practice to test it. Making sure it is reporting virus correctly. On of the simplest tools to use is the European Institute Anti-Virus Research (EICAR) test file.
When researching an attack or a virus don't forget to check the Anti-virus encyclopedia. Most of the Anti-virus vendors have one. They provide detailed information about each virus and clean-up information:
- Virus encyclopedia
- Virus encyclopedia (multi-lingual)
- About Virus (if you have lots of time)
Please also remember that one of the biggest source of propagating virus is actually via social engineering. Many fake virus are circulating via chain letters and form a big time waster. Some good sources for Virus hoaxes are:
- Virus Myths
Friday, August 26, 2005
In security little items like excel sheets are important!
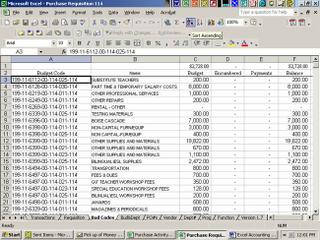 As mentioned in previous posts security is not always about big and well know items like: firewalls, anti-virus, and intrusion detection.
As mentioned in previous posts security is not always about big and well know items like: firewalls, anti-virus, and intrusion detection.When was the last time you audited the critical spreadsheets used through out your business!
In centralized accounting system, everything is entered, tracked, and double logged to avoid fraud. Complete audit trails are kept to ensure any entered information can be traced back to its author.
when you use spreadsheets for critical financial elements of your business you are potentially incurring a big risk. As auditing this format of information is much more difficult if not impossible.
In a very recent story a woman was sentenced to fraud of $2,000,000 from her employer by omitting entries in a spreadsheet.
More details on this story "...She said in a written statement that she posted checks intended for Superior Care, which sells pharmaceutical and medical products, to the company books but omitted them from the spreadsheet she submitted to the billing department..."
Please take note that cause of the risk may not always of a malicious nature. A simple operator mistake of one extra zero missing in a budget planning sheet can also lead to severe disaster during operations stage of you business.
Monday, August 22, 2005
Hacking and hijacking your phone?
 Most of use have become used to protecting your ourselves in hyperspace...: Anti-virus, Firewall, Anti-Spam, Anti-Spyware, anonymizer (prevent identity theft). Most of these protection address issues of varying risk. But in security risk should always be the driving factor for seeking protection.
Most of use have become used to protecting your ourselves in hyperspace...: Anti-virus, Firewall, Anti-Spam, Anti-Spyware, anonymizer (prevent identity theft). Most of these protection address issues of varying risk. But in security risk should always be the driving factor for seeking protection.More and more hackers are shifting their motivation from notoriety and peer symbol status to profit. Along with the change we must now look at new ways to protect ourselves.
One of our friends in Bahrain fell for phone hijacking after getting several months of huge phone bills...Some modem activity was noticed even when no using the computer. After scanning the PC several trojans were found which contributed to this attack.
So what can you do:
- Against phishing attacks (social engineering for profit). Get the netcraft free toolbar.
- Against phone hijacking... Check with your local telco for some protection (some offer automatic account blocking based on threshold limit). Check you bill regularly for unexpected amounts. Be ready to fight the telco. Remember the telco is making money on this so they may move rather slowly so be ready to "pump of the volume".
- Scan you PC to the latest scum, but more advanced solutions exist (more later).
A little more reading here...
Friday, August 19, 2005
Did you forget your badge?
I have yet to address physical security, but one can not have logical security without physical security...

courtesy of Dilbert
Also Dilbert winning quote on physical security from Fred Dales, MS Corp Redmond:
"As of tomorrow, employees will only be able to access the building using individual security cards. Pictures will be taken next Wednesday and employees will receive their cards in two weeks."
More later on physical security...
Wednesday, August 17, 2005
Users are having less time to respond!
 Today's worm attacks re-highlighted the issue of time once again. Today's users and organizations must be much more agile when responding to security attacks. As new vulnerabilities get announced (approximately 5-12 per day) the computing environment must be re-tested for the presence of these vulnerabilities. If their presence is found "Disabling", "Patching" or "Reconfiguration" must take place in a timely manner to avoid further exposure to the new risk.
Today's worm attacks re-highlighted the issue of time once again. Today's users and organizations must be much more agile when responding to security attacks. As new vulnerabilities get announced (approximately 5-12 per day) the computing environment must be re-tested for the presence of these vulnerabilities. If their presence is found "Disabling", "Patching" or "Reconfiguration" must take place in a timely manner to avoid further exposure to the new risk.Today's worm was create and spread faster this its predecessor (Sasser). To some luck the effects were more less performance and some loss or service (since the worm was not actively seeking to destroy data-it could have been much worse). So its time again to learn a very simple lesson...
As as User I therefore recommend the following simple process:
[to be repeated daily--or more frequently if necessary]
1-Download, distribute and Update you virus signatures
2-Check the logs of the firewall and intrusion detection system (personal or corporate)
3-Test your systems for the latest vulnerabilities (specially the critical ones)
4-Apply the necessary Remediation (medicine).
Safe Surf...
Monday, August 15, 2005
More security equals less security?
 Sometimes more security equals less security. There are 3 cases were this simple principle applies:
Sometimes more security equals less security. There are 3 cases were this simple principle applies:1- When we forget security must be implemented by people
2- When the right process is not implemented
3- When the technology for security is faulty
Successful implementation of security is first a people issue. Involvement of people requires building their skills, knowledge and weariness to the correct levels required. The usage of more sophisticate and elaborate technology requires at better skills level to minimize the impact human factor. The human factor elements include human error and exposure to social engineering tactics.
successfully implementation of security requires a continuous and disciplined process. Security process is about repeating day after day the same proven steps without deviation. Perfect is the enemy of good enough (Voltaire was right when he said "perfect is the enemy of good enough...Ô) ... There is no such thing as perfect security, but a security which does not follow the established processes is doomed to failure.
successfullyl implementation of security requires solid and proven security technologies. Lately hackers have moved into taking advantage of flaws in security products. It is important your entire system be secure but also your security technology must itself also be secured. For a long time security companies have taken advantage of security flaws in users computer environments to spread fear and enlarge their sales in the process. With new security flaws being discovered in their products the focus has now been turned on them.
























